Latest Job Opportunities in India
Discover top job listings and career opportunities across India. Stay updated with the latest openings in IT, government, and more.
Check Out Jobs!Read More
SVG and Purrarat threats that attack Ukraine and Vietnam exposed by experts –
Publishing views: 17
“Two threats to attack Ukraine and Vietnam, which experts offer.”
In order to publish Countloader, which is later used to drop Amatera Stealer and Pureminer, a new campaign was seen formed Ukrainian government agencies in the attacks on hunting.
Yurren Wan, Researcher, Fortinet Fortiguard Labs
| According to Yurren Wan, a researcher at Fortinet Fortiguard Labs, “Building emails containing a developed -to -developed graphics files designed to deceive beneficiaries in opening harmful attachments.” |
SVG files are used to start downloading the ZIP package, a password protected containing the HTML Help file (Chm) translated in the attack chains set by the cybersecurity.
The CHM file starts a series of procedures that lead to the deployment of Countloader. Email messages aim to be a notification from the national police in Ukraine. Countloader to empty a variety of loads, including Cobalt Strike, Adaptixc2 and Purehvnc, were recognized, according to the investigation conducted by silent.
However, it is a distribution channel for Pureminer, which is a bitcoin cove. It is important to note that Pureminer and Purehvnc Rat are both the components of larger harmful software suite created by the rituals of the representative of the threat. Here are some additional works of the author himself:
- Purecrypter is an original and .NET encryption system.
- Purerat, sometimes known as Resolverrat, is a Purehvnc alternative to mice.
- Purelogs is the registered thief and information.
- Bluelock is a piece of harmful programs that can download and operate the beneficial loads, operating as a botanite.
- Pureclipper is the scissors virus that uses the attacker’s wallet addresses to replace the encrypted currency addresses that were placed in the portfolio to redirect transactions and steal money.
Pureminer and Amatera Stealer are distributed as attacks without classification, according to Fortinet, and are “implemented via the .net group before time (AOT) with the process of the process cavity or loaded directly in the memory using PythonmoMorymdule.”
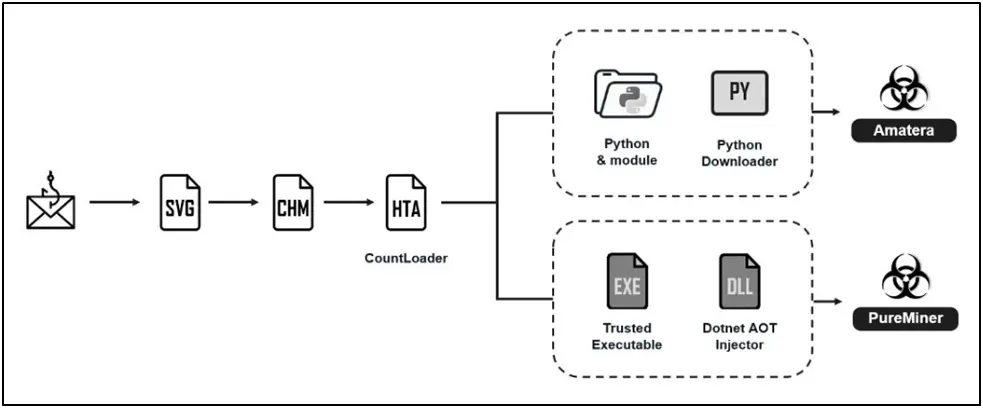
When Amaterra Stealer is operated, it collects system information, files that match with a pre -set list of extensions, information from browsers that rely on chrome and gecko, as well as programs like Steam, Telegram, Filezilla and other encrypted currencies.
Fortinite
| “This hunting campaign shows how the harmful SVG file can serve as an alternative HTML to start the infection chain.” “In this case, attackers used email messages with SVG files to target Ukrainian government institutions. HTML code with SVG Integrated Servies to a download site.” |

This comes after Huntress has discovered a set of threats that are most likely speaking to the Vietnamese and using emails to hunt with copyright notification topics to deceive the recipients in the ZIP holes that launch PXA Stealer, which then develops into a multi -layer infection sequence.
James Nardache, a security researcher
| “This attack has a clear and deliberate development, starting with the attractiveness of basic hunting and progress through levels of defense evasion, theft of accreditation, and the initiatives of memory.” “The conclusion of this endeavor is the final load, Purrarat, which is the professional normative rear door that gives the attack full control over a host.” “They not only show perseverance but also on the characteristics of the ripe and dangerous operator as they are being surrounded by Python frankly to use commercial malware like Purrarat.” |
About the author
Suraj Cole He is a content specialist in technical writing about cybersecurity and information security. He wrote many amazing articles on cybersecurity concepts, with the latest trends in electronic awareness and ethical piracy. Learn more about “him”.
Read more:
The 10 best cyber security news sites to follow up in 2025
About the author
SVG and PureRAT Phishing Threats Attacking Ukraine and Vietnam Exposed by Experts





