Latest Job Opportunities in India
Discover top job listings and career opportunities across India. Stay updated with the latest openings in IT, government, and more.
Check Out Jobs!Read More
Steps stealing 570 GB of Gypper’s private warehouses –
Publishing views: 7
Red Hat confirms the data breach: The militants steal 570 GB from the special warehouses
“The infiltrators claimed that they stole about 570 GB of data from the Gabbab private warehouses, and Reed Hat confirmed this.”
Red Hat, the world’s best open -source software company, has officially acknowledged a dangerous security breach that includes illegal access to the inner Gitlab, which is used by the Red Hat Consulting team.
This confirmation is followed by one of the largest violations of the source law in the history of the last cybersecurity, as the collective actor Crimson Collective claimed the threat that it has been delivered about 570 GB of compressed data from 28,000 private warehouses.
Getlapp’s private warehouse
The GitLab environment used in Red Hat Consulting on some customer’s associations was the explicit goal of infiltration.
Red Hat official statement
| Before the security teams discovered the attack, the unauthorized third party managed to reach sensitive data and successfully copy it from this situation. |
The company immediately started a comprehensive investigation, banned the arrival of the attacker, isolated the affected system, and continued with relevant law enforcement agencies.
Sensitive technical assets such as CI/CD secrets, pipeline formation files, VPN identification profiles, infrastructure plans, ANSIIIILE play books, OpenSHIFT, container registry compositions, and cellar integration secrets in stolen data.
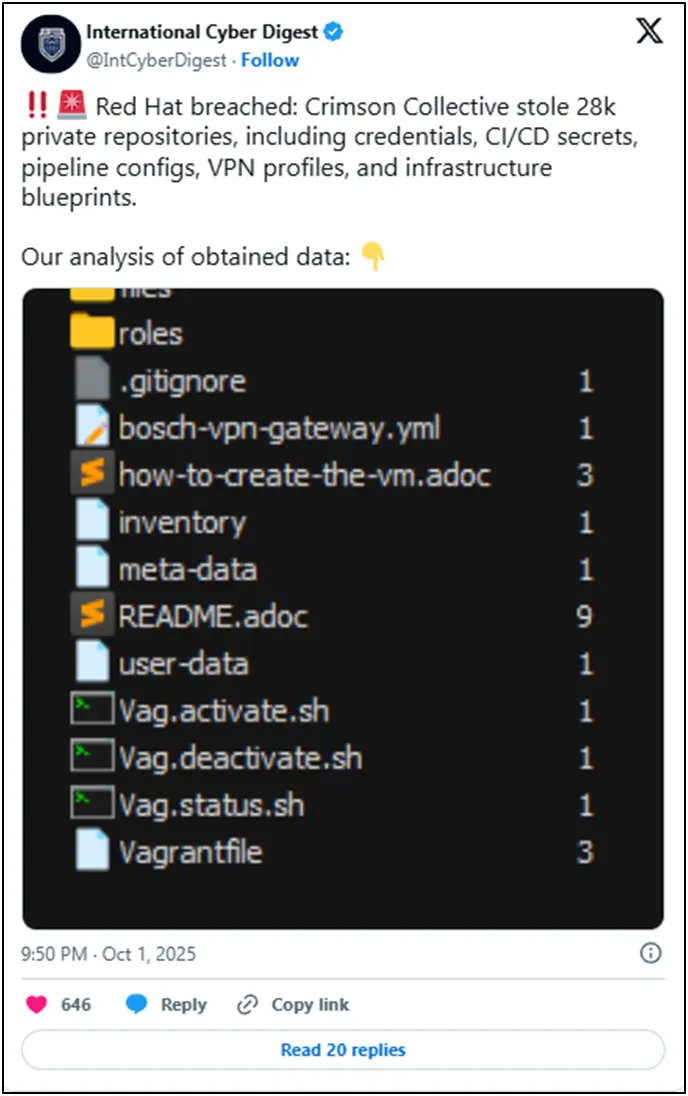
Signs of thousands of organizations were found in a variety of decisive industries by security researchers who examine alleged breach data. These include large financial institutions such as Citi, JPMC and HSBC; Communications giant like Verizon and Telefonica; Industrial companies such as Siemens and Bosch; Even governmental organizations such as the US Senate.
The penetration is an example of an advanced attack of the supply chain that may have an impact on the Red Hat group group.
According to reports, warehouses at risk include configuration of accreditation data management, Devops automation texts, and infrastructure-IC Code molds that opponents may use to experience secondary offside against Red Hat consulting customers.
The actors are the threats that are looking for continuous access to the estuary systems that have many methods of attack due to the inclusion of data at risk of SSH switches, applications interface symbols and database communication chains.
Security experts warn that publishing publishing in Kubernetes may give the configurations of the container record may give the infiltrators comprehensive instructions on how to target the original cloud infrastructure across Red HAT customers.

Since the compositions of GitLab Ci/CD and the automatic publishing pipelines often contain high rights required to publish and maintain institutions programs, cybersecurity experts are particularly interested in exposure to them.
Red Hat said that the initial analysis shows no effect on the official programs distribution channels or the basic software supply chain, and that it has taken additional hardening measures to prevent more unwanted access.
To ensure the full range of the customer’s effect, the work is still analyzing forensic medicine, and any customers will get Red Hat consulting affected by direct notifications.
The recently disclosed CVE-10725 that affects Red Hat OpenSHIFT AI’s services has nothing to do with the accident.
About the author
Suraj Cole He is a content specialist in technical writing about cybersecurity and information security. He wrote many amazing articles on cybersecurity concepts, with the latest trends in electronic awareness and ethical piracy. Learn more about “him”.
Read more:
About the author
Red Hat Confirms Data Breach: Hackers Steal 570 GB of Private GitHub Repositories





