Latest Job Opportunities in India
Discover top job listings and career opportunities across India. Stay updated with the latest openings in IT, government, and more.
Check Out Jobs!Read More
Chinese infiltrators use Rednovember Strike and Pantegana to target governments worldwide –
Publishing views: 39
Chinese infiltrators use Rednovember Strike and Pantegana to target governments worldwide
The representative of the Chinese threat, sponsored by the state, was identified as a source of the suspected electronic espionage activities group that was previously discovered to target international government organizations and the trade sector in Africa, Asia, North America, South America and Oceania.
After monitoring the activities under the name Tag-100, the Future now registered promoted to Hacker Collective Rednoveber. Microsoft also tracks the name Storm-2077.
“Between June 2024 and July 2025, Redenovimber (which interferes with the -2077 storm) targeting surrounds from prominent organizations worldwide and used the Go Go -based Go.
“The organization has expanded the scope of targeting through government and private sector organizations, including defense and space entities, space groups, and law firms.”
The government of Southeast Asia, a European government director, a state security authority in Africa, and the Central Asian Ministry of Foreign Affairs are among the most new victims of the threat representative. European Machine maker, an international cooperation committee focusing on Southeast Asia, is believed to be at least two US defense articles who have been exposed to the group.
More than a year ago, Registered future Publishing the first documents for Rednovember, which described how it used the Pantegana framework after its exploitation and the spark of mice after the well -known security weapons
Disadvantages in a number of peripheral devices facing the Internet from CISCO, Citrix, F5, Fortinet, Ivanti, Palo Alto Networks (Cve-2024-3400), Examination point (Cve-2024-24919), Sonicwall for the first access.

Targeting safety solutions such as loading budgets, protection walls, VPNS, infrastructure for virtual simulation, and email servers are the direction that other Chinese piracy groups sponsored by the country is used more and more to reach interest networks and stay for long periods of time
The use of open source and Pantegana tools is a noticeable component of Tradecraft’s Actor Tradecraft. The adoption is likely to be a step by spying actors to re -display the current programs in their favor and tend to support efforts.
In addition, the attacks use a version of the open source bearing Lizelsader To install the cobalt beacons, a strike or spark of mice on the devices at risk.
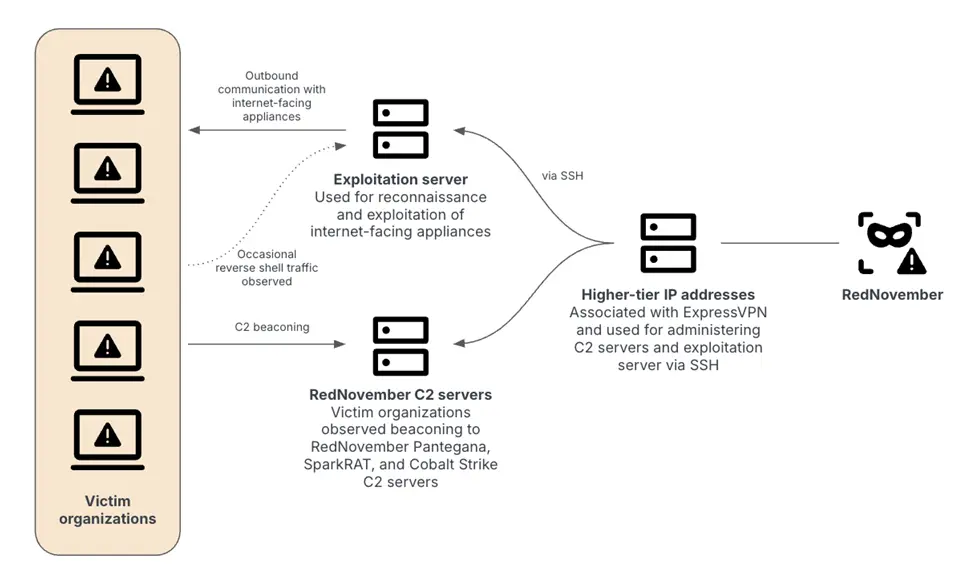
In order to manage and two groups of servers used to exploit devices facing the Internet and communicate with Pantegana, Spark Rat and Cobalt Strike- Another legal program that has been widely used by malicious actors-claims that Rednoveber uses VPN services such as Expressvpn.

The gang of infiltrators focused on most of its targeted efforts on South Korea, Taiwan and the United States and Panama between June 2024 and May 2025. It was discovered to target the Ivanti safe devices connected to a US -based newspaper and engineering and military contractor in April 2025.
Before the state’s visit to the nation of South America to China, the registered future said it has also identified the opponent who was most likely targeting the gates of access to the web of Microsoft Outlook in the country.
“Rednovember historically has targeted a variety of countries and sectors, indicating wide and variable intelligence requirements,” the company stated. “Rednovember’s activity has so far focused on many major geographical regions, including the United States, Southeast Asia, Pacific and South America.”
About the author:
Yogash Naager It is a content specialist in cybersecurity and a B2B area. In addition to writing for news4haackers blogs, it also writes for brands including Craw Security, bytecode Security and Nasscom.
Read more:
Malterminal Malware changes GPT-4 to the ransom program manufacturing unit
About the author
Chinese Hackers RedNovember Use Cobalt Strike and Pantegana to Target Governments Across the World