Latest Job Opportunities in India
Discover top job listings and career opportunities across India. Stay updated with the latest openings in IT, government, and more.
Check Out Jobs!Read More
🔥 Harmful programs on the Chinese people, which include Hidding0st, and Kkrat exploits senior economic officials –
uncovered
Publishing views: 8
“The Chinese people are being attacked by many of the currently harmful program attacks.”
The Seo Poisoning Poison (SEO) targets the Chinese speaking people by publishing harmful programs through false programs.
Pei Han Liao, Labs Researcher, Fortinet Fortiguard
| “The attackers have registered areas similar to the original programs of the original programs and used the additional components of senior economic officials to influence research classifications.” They deceived the victims to reach sarcastic simulation sites and download harmful programs by using convincing language and simple personal changes. |
The Cyber Security Company noticed the activity in August 2025. It leads to the distribution of harmful programs such as Hidding0st and Winos (also known as Valleyrat), which are both differences in Trojan Gh0st mouse.
It is worth noting that the use of Winos is linked to a group of electronic crimes called Silver Fox, which is also known as Swimsnake, Void Archne, The Great Valley (or Thief Valley) and UTG-Q-1000. At least in 2022, it was believed to have been working.
Users looking for programs such as Translate, Google Chrome, Signal, Telegram, WhatsApp and WPS lead to Google to fake web sites in the last series of assault discovered by Fortinet. This causes the Trojans to spread malware.
Fortinite
| “Cute is the name of the text. “The download link is called first, and the text program returns JSON data, including the secondary link, in a multi -step chain. Then, the secondary association leads to another JSON answer with a link that arrested the URL of the malignant fixation. According to Fortinet, “customers found it difficult to discover infection because stabilizers included both malicious loads and original application.” “In this way, the research results were very arranged, highlighting the importance of examining the domain names closely before downloading programs.” |
Delly harmful DLL (“Enumw.dl”) is included in the installer. It performs a number of anti -analysis tests to evade detection, such as another DLL extract (“VSTDLIB.DLL”) to increase the download of analysis tools by increasing memory use and insulting their function.
The second DLL is designed to discover whether the 360 program of antivirus program is installed on the injured host before unloading and releasing the main load. If it exists, the virus determines stability and eventually launches Windows (“Insalivation.exe”) using a method known as Typelib Com Hijacking.
By making the Windows abbreviation indicate the same implementation, stability is done even if the anti -virus program is not present on the host. The ultimate goal of the infection is to organize DLL (“Aide.dll”), which begins three basic operations:
- To communicate with a distant servant and exchange encrypted data, use orders and control (C2).
- Heart pulses, to collect victims and system information and calculate active operations compared to a list of symbolized safety products.
- In order to check stability, monitor the perimeter of the victim, keep the tabs on the user’s behavior, send a beacon to the C2 server.
Orders to download other additions, keys and portfolio information, and even take ETHEREUM and Tether Cryptocurrency Governorate also supported by the C2 unit. It was pre -classified as WinOS ingredients, many additional ingredients discovered have the ability to monitor the victim’s screen.
Trifecta targets harmful programs, Chinese speakers, including new Kkrat#
Development coincides with Zscaler Threadlabz, which defines a different campaign targeting Chinese -speaking individuals and uses Winos, FatALRAT and KKRAT, which is a virus that is not previously documented, as of early May 2025.
Mohamed Erfan VA, researcher, zscaler
| China’s infiltrators are usually used, “which has similarities with both Gh0st Rat and Big Bad Wolf (大灰狼).” According to ZSCaler researcher Mohamed Erfan va Like Ghost Rat, KKRAT uses a network connection protocol, but after data compressing, it adds an encryption layer. Among the features of mice are the implementation of remote monitoring tools (such as Sunlogin and Gothtp) and processing the portfolio to replace the encrypted currency addresses. |
Similar to the aforementioned activities, the attack campaign is distributed by the three Trojan horses by imitating well -known programs, such as Dingtalk, through the pages of fake installations. Since clinic sites are hosted on GitHub pages, criminals may benefit from the credibility that comes with a trusted platform to spread malware. The pages were published using a Github account that is no longer available.
The installed installed on web sites make many checks after the user launches it in order to discover virtual devices (VMS) and sand box environments, and circumvent safety measures.
In addition, he asks about the capabilities of the official, which, if granted, allows them to include and abolish the activation of each network currently in use. This mainly prevents antivirus program from working normally.
The use of your Bring Driver (Byouvd) approach, which includes the reuse of software instructions from the OpenBlindingr Open Source project, to remove installed anti -virus protection, is another observable feature. The following five programs are searched explicitly by malicious programs:
- 360 Internet safety suite
- 360 total security
- Herobravo diagnosis suite
- Kingsvet Internet safety
- QQ 电脑管家
After completing relevant operations related to related viruses, harmful programs continue to create a scheduled task that carries out the textual program of payments with system privileges, ensuring that the operations stop automatically every time the user log in to the computer.
In addition, it changes the Windows Total 360 logs, most likely with the intention of turning off the network examination. Then harmful programs re -create the network transformers to restore the system network connection after completing all these steps.
Schellcode’s launch is the main duty of the stabilizer. This causes the launch of another shellcode symbol called “2025.bin” from the URL encrypted. SEELDCODE, which is recently recovered as Artifact (Output.Log “), which then calls two URLs to recover Zip:
- Zip, contains a legitimate and harmful DLL file launched using a DLL side download
- Zip, contains a file called longlq.cl, which carries the final encrypted load
Zscaler
| “After the legal implementation of TRX38.zip, the malware will briefly make it, add it to the startup folder for stability, then turn on the legal implementation to download the malicious DLL.” “The final load is decoded from the LongLQ.Cl file and is implemented by the harmful DLL. The second postal code package that has been downloaded is the final load of the campaign. “Features like installing RMM facilities such as Sunlogin and Gotohttp, transfer of network traffic that can be exploited to overcome the walls of protection and VPNS, and kidnap the portfolio to replace the currency currency portfolio addresses via KKRAT orders and clothes.” |
The attack chain in the malware campaign that distributes many mice.
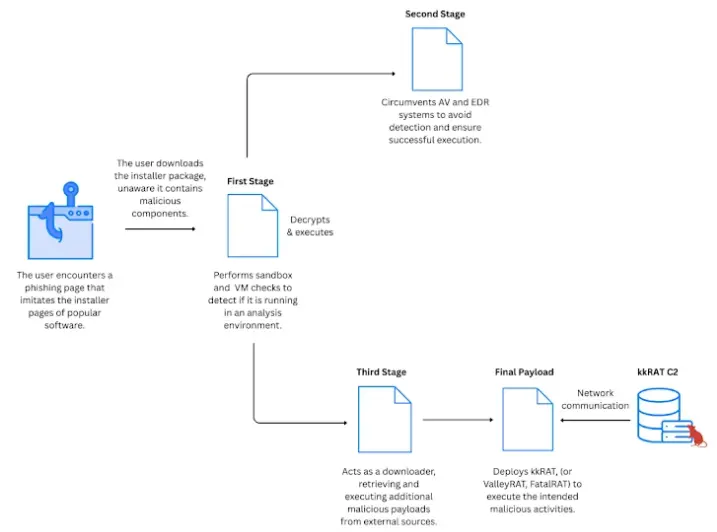
Kkrat is one of the three loads. Once the virus creates a socket connection with the C2 server, it attracts the features of the victim’s computer and gets a number of additions to carry out a variety of data collection operations.
- User input registration and simulation, including mouse movements and keyboard.
- Recover and change data from the portfolio.
- Run the desktop function from remote, such as starting web browsers and off programs.
- Enables the implementation of the command of the document to the shell interface.
- Windows screen management.
- Show the characteristics of operations management, such as the ability to include running operations and stop them when necessary.
- Create a list of all active network connections.
- Provide applications tools, such as the ability to list installed programs and remove some tools.
- Late all the values kept in the automatic registration key and their recovery.
- As an agent for the use of Sockss5 to transmit data between the customer and the server.
In addition to these additional ingredients, KKRAT supports a long list of orders to launch additional ingredients, remove data from 360, Google Chrome, Internet Explorer, Mozilla Firefox, QQ Browser, Sogou Explorer, Skye, Telegram, and work As an authenticity by switching Walkptocrency Walled Collempoor addresses to The Clipboard.
About the author
Suraj Cole He is a content specialist in technical writing about cybersecurity and information security. He wrote many amazing articles on cybersecurity concepts, with the latest trends in electronic awareness and ethical piracy. Learn more about “him”.
Read more:
About the author
📌 Read more at: Full Article
Hashtags: #Harmful #programs #Chinese #people #include #Hidding0st #Kkrat #exploits #senior #economic #officials
📰 Published by daksh kataria on 2025-09-15 12:57:00
Source Feed:
✨ Harmful programs on the Chinese people, which include Hidding0st, and Kkrat exploits senior economic officials –
shared
Publishing views: 8
“The Chinese people are being attacked by many of the currently harmful program attacks.”
The Seo Poisoning Poison (SEO) targets the Chinese speaking people by publishing harmful programs through false programs.
Pei Han Liao, Labs Researcher, Fortinet Fortiguard
| “The attackers have registered areas similar to the original programs of the original programs and used the additional components of senior economic officials to influence research classifications.” They deceived the victims to reach sarcastic simulation sites and download harmful programs by using convincing language and simple personal changes. |
The Cyber Security Company noticed the activity in August 2025. It leads to the distribution of harmful programs such as Hidding0st and Winos (also known as Valleyrat), which are both differences in Trojan Gh0st mouse.
It is worth noting that the use of Winos is linked to a group of electronic crimes called Silver Fox, which is also known as Swimsnake, Void Archne, The Great Valley (or Thief Valley) and UTG-Q-1000. At least in 2022, it was believed to have been working.
Users looking for programs such as Translate, Google Chrome, Signal, Telegram, WhatsApp and WPS lead to Google to fake web sites in the last series of assault discovered by Fortinet. This causes the Trojans to spread malware.
Fortinite
| “Cute is the name of the text. “The download link is called first, and the text program returns JSON data, including the secondary link, in a multi -step chain. Then, the secondary association leads to another JSON answer with a link that arrested the URL of the malignant fixation. According to Fortinet, “customers found it difficult to discover infection because stabilizers included both malicious loads and original application.” “In this way, the research results were very arranged, highlighting the importance of examining the domain names closely before downloading programs.” |
Delly harmful DLL (“Enumw.dl”) is included in the installer. It performs a number of anti -analysis tests to evade detection, such as another DLL extract (“VSTDLIB.DLL”) to increase the download of analysis tools by increasing memory use and insulting their function.
The second DLL is designed to discover whether the 360 program of antivirus program is installed on the injured host before unloading and releasing the main load. If it exists, the virus determines stability and eventually launches Windows (“Insalivation.exe”) using a method known as Typelib Com Hijacking.
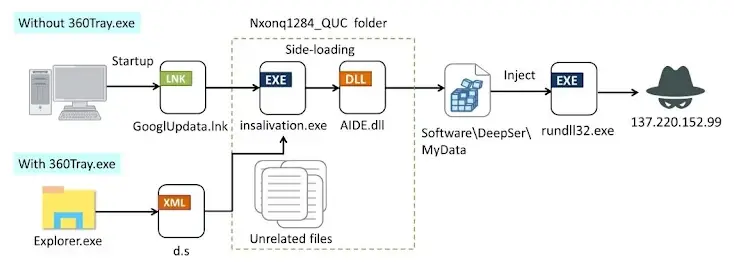
By making the Windows abbreviation indicate the same implementation, stability is done even if the anti -virus program is not present on the host. The ultimate goal of the infection is to organize DLL (“Aide.dll”), which begins three basic operations:
- To communicate with a distant servant and exchange encrypted data, use orders and control (C2).
- Heart pulses, to collect victims and system information and calculate active operations compared to a list of symbolized safety products.
- In order to check stability, monitor the perimeter of the victim, keep the tabs on the user’s behavior, send a beacon to the C2 server.
Orders to download other additions, keys and portfolio information, and even take ETHEREUM and Tether Cryptocurrency Governorate also supported by the C2 unit. It was pre -classified as WinOS ingredients, many additional ingredients discovered have the ability to monitor the victim’s screen.
Trifecta targets harmful programs, Chinese speakers, including new Kkrat#
Development coincides with Zscaler Threadlabz, which defines a different campaign targeting Chinese -speaking individuals and uses Winos, FatALRAT and KKRAT, which is a virus that is not previously documented, as of early May 2025.
Mohamed Erfan VA, researcher, zscaler
| China’s infiltrators are usually used, “which has similarities with both Gh0st Rat and Big Bad Wolf (大灰狼).” According to ZSCaler researcher Mohamed Erfan va Like Ghost Rat, KKRAT uses a network connection protocol, but after data compressing, it adds an encryption layer. Among the features of mice are the implementation of remote monitoring tools (such as Sunlogin and Gothtp) and processing the portfolio to replace the encrypted currency addresses. |
Similar to the aforementioned activities, the attack campaign is distributed by the three Trojan horses by imitating well -known programs, such as Dingtalk, through the pages of fake installations. Since clinic sites are hosted on GitHub pages, criminals may benefit from the credibility that comes with a trusted platform to spread malware. The pages were published using a Github account that is no longer available.
The installed installed on web sites make many checks after the user launches it in order to discover virtual devices (VMS) and sand box environments, and circumvent safety measures.
In addition, he asks about the capabilities of the official, which, if granted, allows them to include and abolish the activation of each network currently in use. This mainly prevents antivirus program from working normally.
The use of your Bring Driver (Byouvd) approach, which includes the reuse of software instructions from the OpenBlindingr Open Source project, to remove installed anti -virus protection, is another observable feature. The following five programs are searched explicitly by malicious programs:
- 360 Internet safety suite
- 360 total security
- Herobravo diagnosis suite
- Kingsvet Internet safety
- QQ 电脑管家
After completing relevant operations related to related viruses, harmful programs continue to create a scheduled task that carries out the textual program of payments with system privileges, ensuring that the operations stop automatically every time the user log in to the computer.
In addition, it changes the Windows Total 360 logs, most likely with the intention of turning off the network examination. Then harmful programs re -create the network transformers to restore the system network connection after completing all these steps.
Schellcode’s launch is the main duty of the stabilizer. This causes the launch of another shellcode symbol called “2025.bin” from the URL encrypted. SEELDCODE, which is recently recovered as Artifact (Output.Log “), which then calls two URLs to recover Zip:
- Zip, contains a legitimate and harmful DLL file launched using a DLL side download
- Zip, contains a file called longlq.cl, which carries the final encrypted load
Zscaler
| “After the legal implementation of TRX38.zip, the malware will briefly make it, add it to the startup folder for stability, then turn on the legal implementation to download the malicious DLL.” “The final load is decoded from the LongLQ.Cl file and is implemented by the harmful DLL. The second postal code package that has been downloaded is the final load of the campaign. “Features like installing RMM facilities such as Sunlogin and Gotohttp, transfer of network traffic that can be exploited to overcome the walls of protection and VPNS, and kidnap the portfolio to replace the currency currency portfolio addresses via KKRAT orders and clothes.” |
The attack chain in the malware campaign that distributes many mice.

Kkrat is one of the three loads. Once the virus creates a socket connection with the C2 server, it attracts the features of the victim’s computer and gets a number of additions to carry out a variety of data collection operations.
- User input registration and simulation, including mouse movements and keyboard.
- Recover and change data from the portfolio.
- Run the desktop function from remote, such as starting web browsers and off programs.
- Enables the implementation of the command of the document to the shell interface.
- Windows screen management.
- Show the characteristics of operations management, such as the ability to include running operations and stop them when necessary.
- Create a list of all active network connections.
- Provide applications tools, such as the ability to list installed programs and remove some tools.
- Late all the values kept in the automatic registration key and their recovery.
- As an agent for the use of Sockss5 to transmit data between the customer and the server.
In addition to these additional ingredients, KKRAT supports a long list of orders to launch additional ingredients, remove data from 360, Google Chrome, Internet Explorer, Mozilla Firefox, QQ Browser, Sogou Explorer, Skye, Telegram, and work As an authenticity by switching Walkptocrency Walled Collempoor addresses to The Clipboard.
About the author
Suraj Cole He is a content specialist in technical writing about cybersecurity and information security. He wrote many amazing articles on cybersecurity concepts, with the latest trends in electronic awareness and ethical piracy. Learn more about “him”.
Read more:
About the author
👉 Read more at: Full Article
Tags: #Harmful #programs #Chinese #people #include #Hidding0st #Kkrat #exploits #senior #economic #officials
📰 Published by daksh kataria on 2025-09-15 12:57:00
Via





